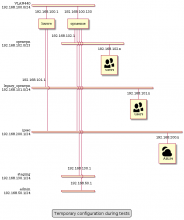
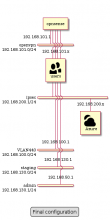
There is actually only one VPN endpoint at Rocquencourt, on louvre.
Louvre has recently experienced a catastrophic failure and had to be rebooted, shutting down all existing network connections.
She will also be moved to a different physical bay, soon, once again shutting down connections for all users.
This can be avoided by creating a different VPN endpoint in Rocquencourt, on a different host.