The new firewall will be deployed and configured for the staging environment.
It will allow to validate the behavior with a non critical environment and will be extended progressively to other environments (admin, production, public ips)
- At the beginning, a single firewall will be used but to prepare a more robust deployment with active/passive instances when the production will enter in the game, the FW will expose virtual IPs as gateway address.
- The internet gateway will be configured to use the new SWH public VLAN (1300) to reach internet
- Some legacy services will be used (DNS server, ...(?))
- A new route must be declared on the current gateway to be able to reach the new staging network (192.168.130.0/24) from the VPN
- The network configuration of the current staging server must be updated to change the network from 192.168.128.XXX to 192.168.130.XXX
This is the identified configuration of the FW before the confrontation with the real world:
- Interfaces :
| Interface | Network | IP | Description |
|---|---|---|---|
| WAN | VLAN1300 | 128.93.166.3 | Public network's interface |
| LAN1 | VLAN440 | 192.168.100.129 | Production network's interface |
| LAN2 | VLAN443 | 192.168.130.2 | New staging network's interface |
| LAN3 | VLAN 442 | 192.168.50.2 | Future admin network's interface (not used in this poc) |
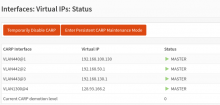
- Virtual IPs
| Network | Ip | comment |
|---|---|---|
| WAN | 128.163.166.2 | |
| WAN | 128.163.166.9 | NAT to staging RP ? |
| LAN1 | 192.168.100.130 | |
| LAN2 | 192.168.130.1 | |
| LAN3 | 192.168.50.1 | |
- Pseudo FW rules identified :
By default, OPNsense allows outbound connections and block inbound connections.
The explicit rules blocking internal network communication should be configured to reject the packet instead of blocking it and have to wait for the network timeout.
Legend:
A <- B : inbound connection from B to A
A -> B : outbound connection from A to B
| Rule | Action |
|---|---|
| staging/ICMP <- production | Allowed |
| production/ICMP <- staging | Allowed (as long as the production network is used by the admin tools) |
| production/DNS <- staging | Allowed |
| production/puppet master <- staging network | Allowed |
| production/icinga <- staging | Allowed |
| staging/prometheus <- production | Allowed |
| production/logstash <- staging | Allowed |
| staging/RP(80,443) <- public/web(NAT?) | Allowed |
| production/sentry(9000) <- staging | Allowed |
| staging/*ssh <- production | allowed |
| wan/RP IP(web) <- production | Allowed (monitoring/access from the VPN) |
| production/keycloak(web) <- staging/webapp | Allowed (SSO) |
| production/ES <- staging/deposit | Allowed(Really needed ?) |
| production/borg(ssh) <- staging | Allowed(backups) |
- connections to internet are allowed by the default outbound allowed rule
- smtp connections to smtp.inria.fr are included in the default outbound rules
- the rules to expose the kafka cluster of the staging environment are not listed here as this cluster doesn't exist yet